TPM to feed random number generator
Table of Contents
One of the uses of a TPM is to feed /dev/random on your linux box. I will not go into the political implications of TPM.
See also Matt Domsch’s blog.
Those still running RHEL5/CentOS5, be sure to have rng-utils-2.0-4 or later and kernel-2.6.18-238.el5 or later.
Some of the following steps are specific to my HP ProLiant MicroServer, but most will apply to any modern linux and HW (one would prefer the TPM to be an integral part of the motherboard as opposed to a module).
Physical installation in HP ProLiant MicroServer
This step will not be necessary on boards which come with a built-in TPM. Security wise, built-in is much preferred but for RNG use it does not really matter. Other motherboards will have a similar procedure.
Follow HP’s instructions in the manual that came with the MicroServer. Remember to not only remove all cables before trying to pull the board out fully, but you also, on the back, remove the screw of any PCIe cards you installed before the tray can be moved at all.
Enabling in the BIOS
All this is done with BIOS 041. I did not test if older versions of the BIOS work.
# dmidecode |grep -A 3 ^BIOS
BIOS Information
Vendor: HP
Version: O41
Release Date: 07/29/2011
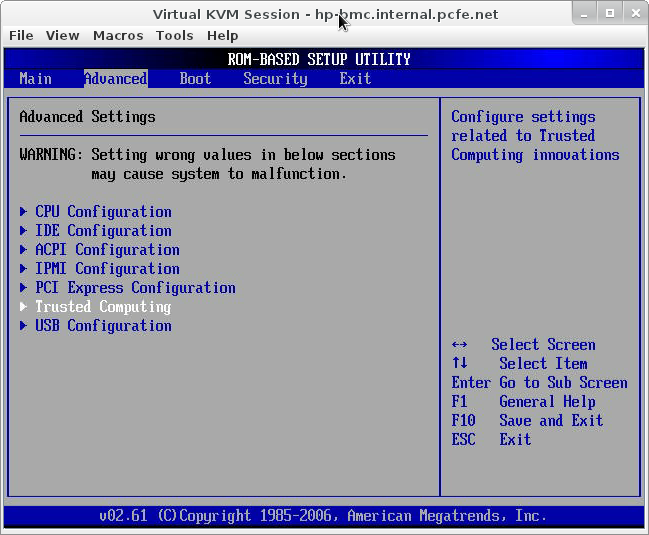
enter BIOS with F10 during POST. Enable it under Advanced Trusted Computing
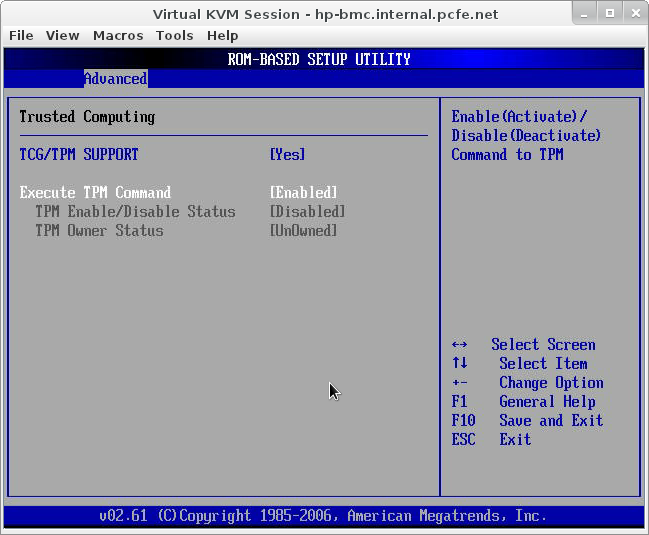
Next time you enter the BIOS, you should see the Status as Enabled. If not, power cycle your box (the documentation is not 100% clear on this being needed or not). TPM Owner Status must be UnOwned when you get the TPM. After YOU took ownership, it will show up in the BIOS. If you are the owner of a machine, and just installed a TPM that shows it’s owned, you have other problems than getting your random number generator fed. Go find out what happened with the TPM you have before you. Keep in mind that on certain machines you will be the user but not the ownwer (e.g.: a machine supplied by your employer). If this is not clear to you, please read up on TPM
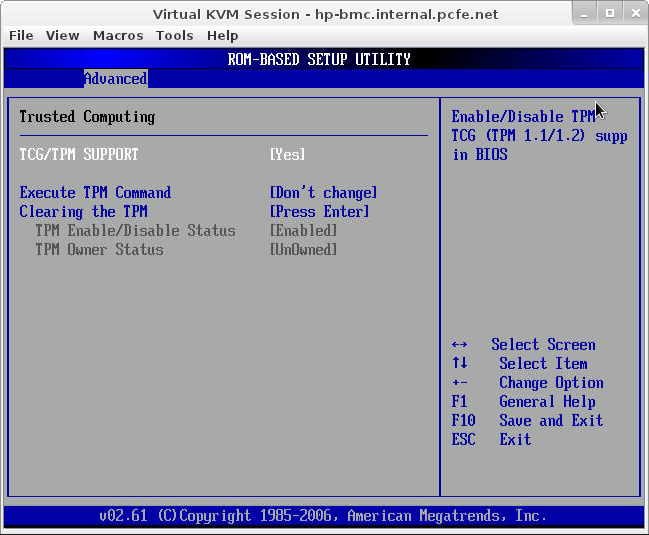
taking onership of the TPM within linux
While I did all this under RHEL6, any modern distro should support this. FWIW, I did the same under Fedora a while ago on my ThinkPad x60. Install needed software:
# yum install tpm-tools rng-tools
The vendor manual only speaks about Windows software and how to take ownership of the TPM with it. HP does recommend reading the HP Trusted Platform Module Best Practices White Paper but I somehow fail to locate that document on HP’s site. Do leave a comment if you know where it can be obtained.
After the machine boots, you should see /dev/tpm0, if not, verify your BIOS settings.
It is imperative that you read and understand tpm_takeownership(8) before continuing.
# man tpm_takeownership
Now claim ownership of your TPM.
# service tcsd status
tcsd is stopped
# tpm_version
Tspi_Context_Connect failed: 0x00003011 - layer=tsp, code=0011 (17), Communication failure
# /etc/init.d/tcsd start
Starting tcsd: [ OK ]
# tpm_version
TPM 1.2 Version Info:
Chip Version: 1.2.3.17
Spec Level: 2
Errata Revision: 2
TPM Vendor ID: IFX
Vendor Specific data: 03110008 00
TPM Version: 01010000
Manufacturer Info: 49465800
# tpm_takeownership
Enter owner password:
Confirm password:
Enter SRK password:
Confirm password:
For the aim of feeding /dev/random, we could also take the well known passwords. You did read the man page, right? But why set well known ones when you can have your own?
If you plan to use software that expects the passwords to be in unicode, use the --unicode flag. Read /usr/share/doc/trousers-*/README for details.
While we did activate tcsd to be able to take ownership, “tcsd is a user space daemon that should be (according to the TSS spec) the only portal to the TPM device driver.” from tcsd(8). As such, you have to choose between rngd and tcsd. We only use the TPM to feed the entropy pool and disable tcsd.
# chkconfig tcsd --list
tcsd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
# service tcsd stop
Stopping tcsd: [ OK ]
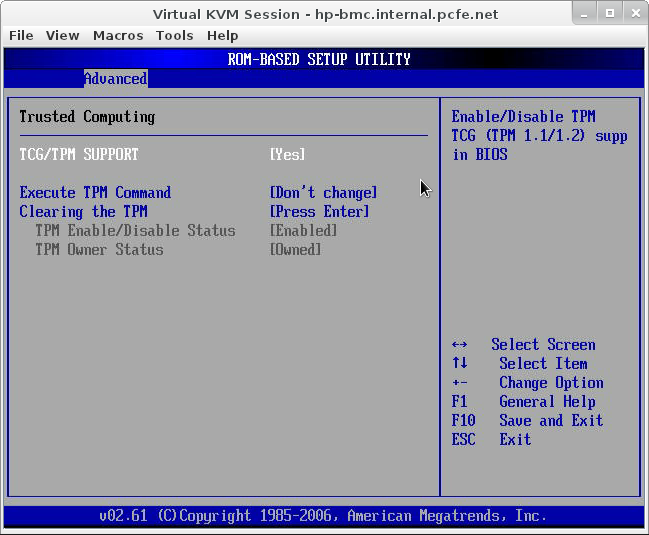
After taking ownership, your BIOS will show;
using the TPM to feed the RNG
Now, first get a baseline when rngd is not on.
# cat /dev/random | rngtest -c 1
As this will be very slow, we check only 1 block. But ideally you’d check 100.
Now manually launch rhgd (in background mode) and check the rngtest results against your baseline.
# /sbin/rngd -b -t 1
# cat /dev/random | rngtest -c 100
It’s OK to test 100 blocks now.
If you do not get dramatically better values for input channel speed something went wrong.
to be sure rngd uses /dev/tpm0, strace it and look at the open calls with -etrace=open
Do keep in mind that a TPM is no speed daemon, expect to see an input channel speed in the Kibits/s range. Mine gives about 90
enabling at boot
Bug 215371 being closed, I just enabled this in rc.local. N.b. the init script attached to that bug is not TPM specific, so do not blindly use that. Comment 8 in bug 130350 explains why this is not enabled by default. Anyway, if your distro of choice also does not run rngd at boot, do something along these lines;
cat <<EOF >>/etc/rc.local
# rng-tools has no init script
# c.f. RHBZ 215371 and RHBZ 130350
# launching now to feed the RNG via the TPM
/sbin/rngd -b -t 1
EOF
available entropy
You can check how much entropy is available with
# cat /proc/sys/kernel/random/entropy_avail
use for KVM guests
kernel 2.6.25 or later has virtio-rng.ko but all my guest machines run older kernels, so I can not test this. See here.
addendum
on the quality of the generated random numbers and the overall security assessment of TPMs
I got this from a colleague, who is more knowledgeable in this field than me, in response to the question “My only concern how is how secure these black boxes really are.. perhaps /dev/urandom is more secure, given it’s at least been peer-reviewed and scrutinised.”
As with all HSMs, its owner cannot directly check the HSM’s firmware and chip-design. BTW, the latter applies to almost all hardware, e.g. also all hardware-RNGs in CPUs or southbridges.
As manufacturer-documentation can be deemed to be not very trustworthy (even without any conspiracy-theory, it is clear that their marketing always intends to state that the delivered entropy is “perfect”), although some docu is quite extensive and comprehensible (e.g for VIA’s Padlock), that is what Common-Criteria evaluations are for:
A Protection-Profile (PP) is written. For the TPM 1.2 the TCG has written the PP and published it on their web-site, as it must be accesible for TPM-owners in order to comprehend the details of the security asessments provided by a CC-evaluation. A PP defines…
the Target-of-Evaluation (TOE): Which parts of the whole security-system are evaluated (here: the TPM, but not its hardware-interface or any host-side hardware or software, e.g. host-firmware or -driver talking to the TPM).
the security targets: Which kind of attacks to protect against.
the security functions: which specific functions of the TOE are inspected.
the methods and depth of the evaluation by choosing an EAL-level defined by Common-Criteria.org (here: EAL4 with three additional methods from EAL5, hence EAL4+)
Manufacturers submit their TOE (here: a specific TPM-model) along with evaluation-documentation (at anything higher than EAL4, basically the complete hardware- and software-design) to an independent, CC-accredited test-lab, which evaluates the TOE according to the PP and writes an evaluation-report.
A certification-authority for CC-evaluations (e.g. NIST, the german BSI, the french ANSSI, chosen by the TOE-manufaturer) checks the evaluation-report for correctness (formal and technical) and results, and publishes a CC-certificate.
In short: Yes, the HW-RNG in a TPM 1.2 part of the TPM-PP’s TOE, and its security-target (i.e. quality of entropy) is defined there. There are CC-certified TPMs (with the TCG-PP, and in case of STM also with a different PP @EAL5+), e.g. by Infineon.
Fedora 17 and later
install kernel-modules-extra if your tpm’s module is not under /lib/modules/…/extra/drivers/char/tpm (I had to do this for tpm_tis, needed for my ThinkPad x60)
you no longer want an rc.local entry, you can use
# systemctl enable rngd.service
kudos
- dcleal for pointing out this feature
- Florian for explaining how the TPM works in depth
- Dell for writing the upstream patches that add tpm rng support to rngtools
- the unnamed colleague who provided more info on the security evaluation
to do
- find out how to get rngd to read via trousers’ tcsd